
ANALYSIS OF FOREIGN VIDEO AND AUDIO RECORDINGS
As soon as foreign enemy recordings are posted on websites a number of teams within
intelligence circles begin their analyses of the various components of the recording.
Some scrutinize the wording looking for patterns and coded message, some analyze
the voices. and others observe the properties of the electronic file. Under certain
circumstances even the power line frequency can be detected to aid in determination
of location where the recording was made. Yemen, for example uses 50 Hz power
while we, in the U.S. use 60 Hz.
Teams examining new tapes:
1. Voice identification – Electronic Analysis
2. Voice identification - Speech Patterns, and vocabulary
3. Crypto Team – Analyzing possible imbedded messages to cells
4. Electronic Team – Looking for clues as to time and location
Intelligence Analysis of New Tape
Voice Identification - Electronic
. Comparison with known voices
Voice Identification-Human Review
Crypto Team – Computer Analysis
. Letter, word, and phrase count
Electronic Tests
Video Analysis
Finally, tests are performed to detect any hidden digital messages or files
within the audio or video file. Any posted file can contain secret messages.
DEMONSTRATION OF STEGANOGRAPHY
(the concealment of secret messages within a file)

Above is an innocent looking JPG file.
Now, using special software, I have embedded a secret message, actually three, within the JPG file.

It looks the same, right? That's the idea of Steganography. It is the process by which
a hidden message can be transmitted without making anyone aware of its existence.
Decoding, we obtain:
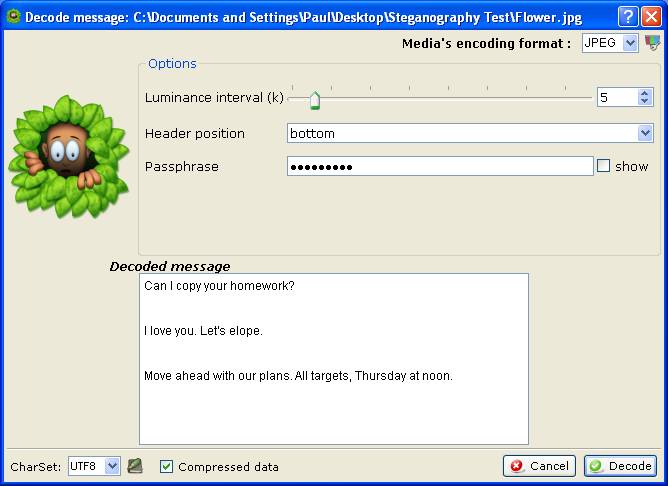

The first two messages seem harmless enough. It is the third message that is troubling.
The question is, do Youtube and Hulu, etc. scan the uploaded files for secret content?
And does the Government have any input in doing this? Food for thought.
For more information contact:
Paul Ginsberg, President
Professional Audio Laboratories, Inc.
www.proaudiolabs.com
@ProAudioLabs
(914) 263-8010